What is a Denial of Service Attack: Prevention Tips
Last Updated on 1 month by Touhid
A denial-of-service (DoS) attack is a malicious attack where legitimate users are unable to access computer systems, services, or network resources. The service may be websites, online web-based applications, email, financial software, and other applications. In this post, we will discuss, what is a denial of service attack and how to prevent a denial-of-service attack.
Table of Contents
What is a Denial of Service Attack?
A denial of service attack or DoS attack is a type of cyber-attack that shuts down a system or network and makes the system unavailable to its intended users.
In a DoS attack, the attacker floods the target system by sending massive amounts of traffic and the system is unable to access it, resulting in a denial of service attack. In that case, legitimate users such as employees, visitors, and members are unable to access the system until the normal traffic is processed.
There are several signs or symptoms when a DoS attack happens, which are as follows:
- Unavailability of Websites or applications.
- Degradation of network performance.
- Receiving the usual volume of spam emails.
- Inability to access a website.
We know that phishing is a type of cyber-attack, whose main aim is to steal sensitive information, but a Denial-of-Service attack doesn’t usually do that.
The main target of a DoS attack is the loss of reputation of an organization. The organization may be the top level of the country such as government, banking, commerce, and other financial sectors.

What is a Distributed Denial of Service Attacks (DDoS) Attack?
A DDoS attack is a cyber-attack that interrupts normal traffic to a targeted website, service, server, or network. In a DoS attack, the malicious data or requests are sent from a specific source but in a DDoS attack, the malicious requests are sent from multiple systems or sources to disrupt the services.
Typically, DDoS attacks involve many “zombie” systems. The “zombie” or “bot” is a compromised computer or network that has previously been compromised and controlled by an attacker or malware.
Then the “zombie” sends massive amounts of malicious data or requests to a targeted website, service, server, or network to disrupt the services.
Difference between a DOS attack and a DDoS attack
Already we know what is a denial of service attack and DDoS attacks. Now, in this section, we will discuss the main difference between a DoS attack and a DDoS attack.
A denial-of-service (DoS) attack uses a single computer or machine to flood a targeted server, while a DDoS attack uses multiple computers or machines to flood a targeted server.
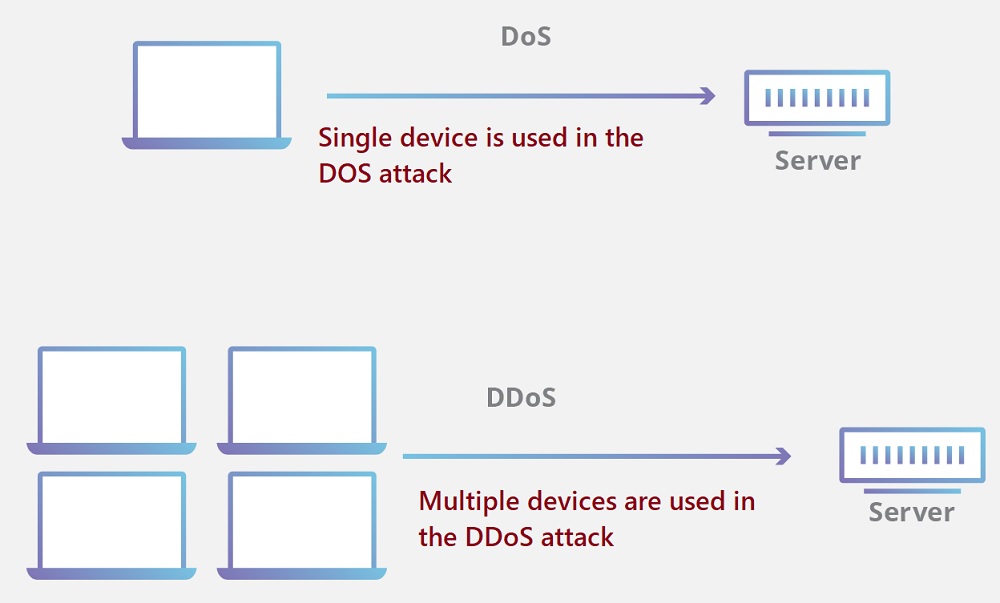
However, the other difference between a DoS attack and a DDoS attack is as follows:
| DoS attack | DDoS attack |
| It is easy to trace the DOS Attacks | It is very difficult to trace the DDOS Attacks |
| The attacking system of a DoS attack is slower as compared to a DDoS attack. | A DDoS attack’s attacking system is faster than a DoS attack’s. |
| Only one device is used in the DOS attack | But in a DDoS attack, multiple devices are used at the same time |
| The traffic volume of a DoS attack is less as compared to a DDoS attack. | The traffic volume of DDoS attacks is massive as compared to DDoS attacks. |
How Does a DoS Attack Work?
Whenever a DoS attack happens, it can last a few hours to one or more months and the resources and services are unavailable to access. Typically, a DoS exploits the software vulnerability and consumes available hard disk space, memory, or CPU of the server.
A DoS attack can be executed in two ways.
First way: In this way, the cyber attacker exploits the vulnerabilities of an application by sending malicious files and bringing down the system. In that case, the regular users are unable to access the system.
Second way: In this way, the attacker sends rapid and excessive unwanted traffic requests to a target server from one device to overload the server’s bandwidth, resulting in denial-of-service attacks.
Types of DDoS Attacks
There are three types or techniques of DDoS attacks, which are as follows:
- Network-centric or volumetric attacks
- Protocol attacks and
- Application layer Attack
Network or Volumetric Attacks
Volumetric attacks are common types of DDoS attacks, where the entire bandwidth of a network is consumed. Once the bandwidth has been consumed by an attacker, then authorized or legitimate users will not be able to access the resources within the network.
Volumetric attacks happen when the attacker floods the network devices such as hubs or switches with ICMP echo requests until there is no more bandwidth available.
In volumetric attacks, the attackers send a huge number of malicious requests to the target system in order to overwhelm the network equipment, servers, or bandwidth resources.
Protocol Attacks
The Protocol attack is another denial of service attack, which focuses on exploiting a weakness in Layer 3 or Layer 4 of the OSI (Open Systems Interconnection) network model.
Typically, this type of attack consumes the capacity of the web server’s resources or any other network hardware such as firewalls and load balancers. Finally, the result is an inaccessible service to the intended users.
Application Layer Attack
Application layer attacks are a type of malicious attack designed to flood specific applications to slow or crash the application. So, the applications are unable to deliver content to the intended user.
In an application layer attack, the attacker floods the target system by sending millions of traffic to a particular service and the system is unable to access it, resulting in a denial of service attack. The most common target of attackers is web servers.
This layer is also known as “top” layer 7 (L7) in the OSI network model and is closest to the end user’s interaction. In this layer, internet requests such as HTTP GET and HTTP POST take place.
How to Prevent Denial of Service Attack
It is very difficult to prevent DoS attacks. However, here are the best recommendations on how to prevent denial of service attacks.
- Purchase More Bandwidth
- Protect DNS Servers
- Use Network Firewall and Web Application Firewall
- Maintain a Strong Network Architecture
- Configure Network Hardware
- Build Redundancy into Your Infrastructure
- Deploy A DDoS Protection Appliance
1. Purchase more Bandwidth
The first and key tip to avoid a DoS attack is to purchase more Bandwidth. You have to ensure that you have enough bandwidth to handle any kind of malicious traffic that can disrupt services.
Since the attacker consumes the bandwidth in the entire network to interrupt the service so, you have to purchase sufficient bandwidth to run the service.
However, this is a safety measure to run your service, but not a DoS attack solution.
2. Protect DNS servers
Cyber attackers are very smart with new technology. They can shut down your website, application, and web servers by attacking DNS servers. If the attacker can get access to your DNS servers then, they can shut down your all websites and web servers.
That’s why you must ensure that you have redundant DNS servers and are connected to different networks. It is better if you place the DNS servers physically (in several countries/regions) in different data centers.
3. Use Firewall
To protect from denial-of-service attacks you should use network firewalls, web application firewalls, and load balancers in your data center.
A web application firewall (WAF) is an application-based cyber security tool that is designed to protect websites, and applications by filtering and monitoring HTTP harmful traffic between a web application and the internet.
WAF will protect your websites, applications, and web servers. It will allow legitimate traffic and block malicious traffic.
The most used Web Application Firewalls are as follows:
- Fortinet FortiWeb
- Citrix NetScaler App Firewall
- F5 Advanced WAF
- Radware AppWall
- Symantec WAF
- Barracuda WAF
- Imperva WAF
- Sophos XG Firewall
- SonicWallNSa
4. Create a Strong Network Architecture
It is very important to secure your network architecture in order to protect from DoS attacks or other malicious attacks. You may secure or create strong network architecture by using the following tools and techniques:
- Keep Your Systems Up to Date.
- Use Antivirus and Firewall Solutions.
- Use a web application firewall.
- Maintain the Load balancing of the web server.
Every organization should have redundant web servers, hardware, and network resources to smooth the running of the services. If one server is attacked by an attacker, then other servers can handle or operate the network traffic.
5. Configure Network Hardware
If you have a firewall or router in your network, then you need some configuration changes that may protect you from DNS and volumetric attacks. When you configure your firewall or router then simply block the DNS responses from outside your network or drop incoming ICMP packets.
6. Build Redundancy into Your Infrastructure
If an attacker can successfully initiate a DDoS attack against your web servers, then the result is an inaccessible service to the end users. So, it is very important to build multiple data centers such as redundant network and hardware infrastructure.
It is essential to ensure that the data centers are geographically in different locations and should connect with different networks.
However, if one data center is affected by malicious traffic then other unaffected data centers can handle the legitimate traffic.
Bottom Line
A DoS attack occurs when intended users are unable to access services such as email, websites, applications, online accounts, or other services. It has an impact on organizations both time and cost when their services are affected and inaccessible to the users.
Finally, if you implement the suggested tips, then you can easily avoid and stop denial of service attacks. Hope the article “What is a denial of service attack” and all topics related to the DoS attacks will be helpful for you!!!




